In order to protect your computer from a new type of malicious software, please close your applications and turn off or restart your computer before you go home today. Ransomware is a new category of malware (malicious software) that infects and holds its victim’s computer hostage until money (ransom) is paid. Cryptolocker, a recent and particularly nasty strain, has been affecting an increasingly large number of individuals, businesses, and other organizations.
A malicious PDF attac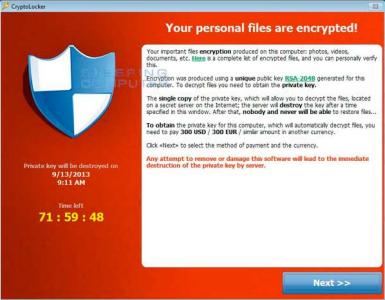 hment in an email appears to be the usual source. Once a computer is infected, the malware begins a process of encrypting or locking documents and other user files on local and mapped drives (i.e. the G: drive). Once encrypted, those files are inaccessible until a sum of money is paid in exchange for the decryption key. In the case of CryptoLocker, this sum can be $300 or more. Unfortunately, payment of the ransom is no guarantee affected files can be made recoverable.
hment in an email appears to be the usual source. Once a computer is infected, the malware begins a process of encrypting or locking documents and other user files on local and mapped drives (i.e. the G: drive). Once encrypted, those files are inaccessible until a sum of money is paid in exchange for the decryption key. In the case of CryptoLocker, this sum can be $300 or more. Unfortunately, payment of the ransom is no guarantee affected files can be made recoverable.
As of today, no commercially available antivirus software will unlock or repair encrypted files once this malware attacks.
Be alert
Once again, everyone is urged to be vigilant, particularly concerning attachments and links in email. Unless you are expecting an attachment from a sender, any attachments received should be treated as suspicious and left unopened. This is especially true for unsolicited messages from unknown senders. In the case of malware like CryptoLocker, an ounce of prevention is worth a pound of cure.
CryptoLocker prevention — please shut down and reboot your computer
UFV IT Services is taking a number of steps to protect UFV users from CryptoLocker. One of those steps involves updating a local computer policy on all UFV workstations. This computer policy update requires a reboot in order for it to take affect. Please take a moment before the end of the day to close down your applications and restart your computer.
Christopher Jones,
IT Security Analyst
IT Services will never ask you to divulge your log in credentials or complete a form via email. All such requests are illegitimate and should be ignored or deleted.
